I noticed that whenever I clicked on my D drive of Windows 2000 server to open a data files (As I stored Server OS and other software on C: drive only) I got message which indicated that “Windows cannot find copy.exe”. Make sure.........................
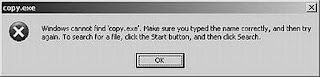
Surprised! As far as my knowledge says Copy is an Internal command of DOS and it is built in Command.com file. I have never seen any copy.exe file in Windows folder at all. Then what prompted OS to show this message?
After few seconds, the warning bells started ringing in my mind. Might be a virus!!!
So without wasting of mush time, I goggled for copy.exe and it confirmed that it is nothing but SALGA.A worm
I immediately clicked on my Clamwin anti virus button. Clamwin is the antivirus which is not only open source, free but also run on Windows 2000 server too. AVG FREE and other free antivirus doesn’t run on server editions of windows ,a s they are free for personal use.
Clamwin detected this virus and clean it. I restarted the system. After ten minutes, again I got the same message “Windows cannot find copy.exe”.
Means Clamwin did not clear it. May be a false message of removal.
Again I searched on goggle. I read many articles then finally I came to across the utility called “Perlovga Removal Tool”.
I download this tool from http://en.sergiwa.com/modules/mydownloads/ and to my surprise it was just 36 KB.
I run this file and within few seconds it gave me the message that it cleaned all the copy.exe files from entire system
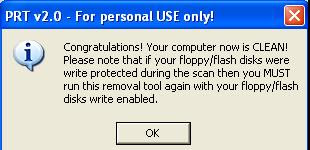
I couldn’t believe it. So I created a dummy copy.exe file in deeply rooted folder of F drive and I run again this utility. As usual within few seconds, it indicated that it had removed copy.exe file. I checked the folder in F” drive and Voila… Copy.exe was not there.
I restarted the system and so far I haven’t received the copy.exe error message yet.
So it was PRT Perlovga Removal Tool , which solved the copy.exe problem.
Note: I read that this worm get spread through USB flash drive via autorun.exe files. I also noticed that it creates Temp.exe files too. The best method for removal is to start the system in Safe mode and run this tool.
But the big question is “ Why Clamwin has not detected it when I plugged USB drive to server.
Answer is very simple: ClamWin does not yet automatically scan files as they are read and written , automatically in real time. It detects only when u run it Intentionally
More info: http://forum.kaspersky.com/index.php?showtopic=29779
No comments:
Post a Comment